RFID Controlled Server Access Proposal
11/17/22-12/12/22
Samuel Lee syl59 & Shuxian Jiang sj688
Demonstration Video
Introduction
In the final project, we designed an RFID system for Cornell students to access to the Raspberry-Pi. From the Figure 1, we can learn that the system would allow students who are in the allowed list to log in by scanning the card and then they can communicate with each other after they have logged in. Considering security and privacy, we set up SSH before students log in. Meanwhile, the data such as Student IDs about students would be recorded for the administrator to manage the RFID system. The administrator who has supreme authority can kick off the users physically without permission of users. Moreover, we also designed a GUI on the Raspberry-Pi to control the system more efficiently.
Project Objective:
This project focused on adding an RFID sensor to a SSH server for increased security. In order to access the system, users would need to scan their attached RFID tag. A GUI was developed for direct control over the users using the PiTFT, as well as a basic chat system for the users to communicate.Design and Testing
In this project, the server would run on the Raspberry-Pi so that we need to install GUI, RFID sensor etc. on it. The main process for our final project lasts 4 stages. In the first stage, the task is to set up the PiTFT GUI using Pygame based on the rolling_control of lab3 with more layers to the UI. We need to shorten the length of code since there are a fair number of new layers and buttons added. And then we install the multi-user server as the foundation for the construction of RFID system. This system is a prototype where a handful of students are for testing so that the memory of sd card is large enough for our RFID system. However, an external drive is likely necessary to store data when it is applied to a real system.
In the second stage, we complete chat system for users and assembling the hardware of RFID sensor. It is more complicated than anticipated when we work on the chat system for the reason that replacing the response messages with input lines required using some special characters which have the side-effect of sometimes causing buggy outputs. Additionally, ensuring the fluency of communication is also essential so we threaded the keyboard interrupt so messages are sent to the corresponding FIFO queue using echo, while the main thread is free to write to the terminal screen without blocking. As to the hardware assembling, we soldered the pins onto RFID board, paying attention to high temperature of soldering iron and ensure the melted tin separate incase of short-circuiting. And after accomplish assembling, there are three modes, IC2, SPI, UART to select to work and we eventually decide to work with UART due to existing usage of the SPI input for the PiTFT. We wired the circuit as the Figure 2 displayed.
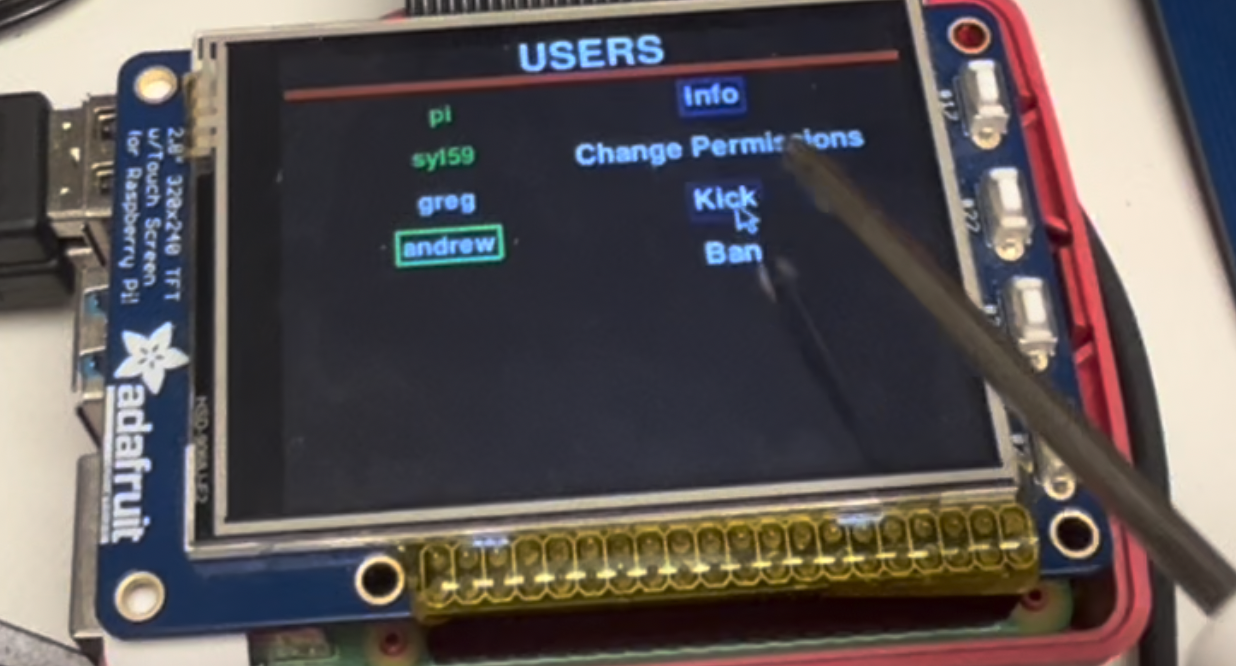
The final two stages consisted of creating the SQL database to store the user information such as username, RFID tag, and permissions and integrating everything with the ssh system. This required some trial and error to find a version of SQL that would install properly on the raspberry pi, and we eventually found mariaDB. Once that database was set up, we created a python utility file with a list of functions for accessing and modifying the users table. Using this utility file, we created a register_user.py script to register a user with a given RFID tag, and input that data into the database. Once the SQL database was set up, we moved on to the final step, which was to connect functions from the GUI and the RFID authenticating code with the SQL database and with the larger SSH system. Kicking a user required killing all processes assigned to that user, which created some issues, and banning them was as simple as changing their permissions in the SQL table.
The GUI and chat system were originally developed and tested on a personal computer for convenience. The GUI was tested using a mouse instead of a touchscreen, while the chat could be tested in a similar manner to how it would be used on the SSH server. The GUI went through a fairly lengthy iterative process, mainly to ensure that the buttons were highlighted properly and to update the user list when a user was kicked. Testing the RFID sensor had to be done on the raspberry pi, and we tried multiple different communication protocols before we realized that UART is the only one that would work with the setup we had, as the PiTFT restricts other devices from using SPI. After trying many different implmentations of UART code in python, we eventually found pynfc, a python library for reading RFID scanners and other similar devivces using a raspberry pi. The success of this library saved us from having to read the RFID scanner's datasheet to manually cosntruct the UART signals. To integrate the RFID scanning code into the login flow, we made a call to the RFID sensor code at the end of the master bashrc file, so that every new terminal connection would be forced to run it. To ensure that users could not quit the program to circumvent the RFID authentication, we checked the exit code of the program. The exit code was only 0 if the program exited via a correct RFID authentication, so if the code was not 0 then we kicked the user off the system by killing all of their processes. This worked very well, but it caused an issue once when opening a new terminal tab on the raspberry pi. We accidentally used the wrong RFID card assigned to the "pi" user, which immediately terminated nearly all running operating system processes. To prevent this from happening again, we added a special case in the code for the pi user to skip the RFID authentication altogether. In order to control which users can acceess the system, we originally used the AllowedUsers configuration option in the sshd_config file, but we realized that updating that file did not immediately affect a user's abiity to log into the system, so we instead added an additional possible user role, "BANNED", which would indicate that a user was banned from entering the system. During the RFID check code, we also checked the users's role to ensure they were not banned.
Drawings
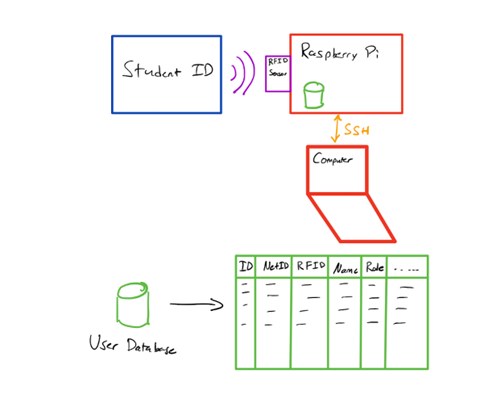
Figure 1: Diagram of RFID system
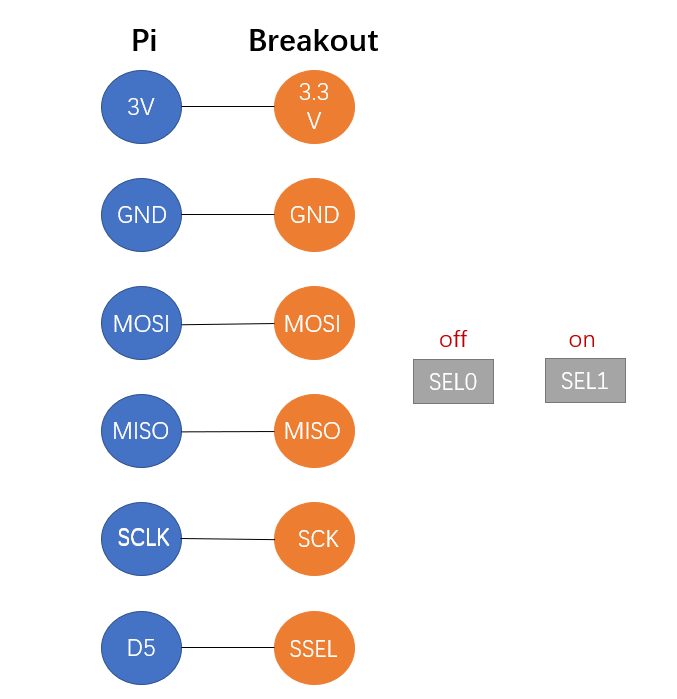
Figure 2: Circuit of Raspberry-Pi with SCI
Results
At the end of this project. We have finished the construction of RFID system for students and tested it. It proves that RFID system can work successfully where students are able to login and logout if they are allowed to enter. They can communicate with each other online only if they have access to the system. From the backend, the data of students has been recorded and the administrator does not need permission of students to kick off students. To sum up, we have accomplished the initial plan almost. However, as planned, we also need to add VPN function for users. And we cannot connect to VPN even though we have installed the VPN sever on the Raspberry-Pi. We have checked the version, time zone, firewall, faults of configuration file, logs and so forth, but the reason for misconnecting is still unclear. Therefore, it is necessary to make more exploration to have VPN connected.
Conclusion
This project shows a basic RFID authentication system for a raspberry pi SSH server, with some added functionality (the chat system) and a GUI administrator console for control over users on the system. This proof of concept could be expanded to a real system with more security measures in place, and if a VPN is used it could be protected from unauthorized accesses.
Work Distribution

Sam Lee
syl59@cornell.edu
Designed the overall software architecture.

Shuxian Jiang
sj688@cornell.edu
Tested the overall system.
Parts List
- Raspberry Pi $35.00
- AdaFruit PN532 RFID Sensor $39.95